- Why Developers Need Access to IBM MQ
- The Challenge: Security and Compliance Limit Developer Access
- Infrared360: Putting MQ in Developers’ Hands (Safely)
- Trusted Spaces™ Explained: Role-Based Access Without Risk
- Real-World Results: Faster Dev, Fewer Tickets
- Getting Started with IBM MQ Developer Edition
- Back to That Queue You Couldn’t See…
Why Developers Need Access to MQ and How to Make It Work Securely
Imagine you’re a developer trying to test a new feature that sends a message through IBM MQ.
You write the code, hit run… and nothing happens. The message disappears. You suspect it’s stuck in a queue somewhere.
But you can’t see it. You can’t confirm it. And you definitely can’t fix it, because you don’t have access.
That’s the daily reality for development teams across many large enterprises. IBM MQ is powering critical applications, but the people building those applications are often flying blind. Developers are stuck filing tickets, pinging admins, or waiting on screenshots just to confirm if a message made it into the queue.
It’s not that admins want to be gatekeepers. They’re protecting high-stakes infrastructure governed by strict compliance policies. But when MQ access becomes a bottleneck, progress slows, teams get frustrated, and delivery timelines stretch.
What if there was a way for developers to access IBM MQ—securely?
What if they could test, validate, and debug messaging flows without putting production at risk?
In this post, we’ll break down why developer access to MQ matters, what’s standing in the way, and how some teams are finally solving this challenge, with fewer tickets, faster cycles, and complete compliance peace of mind.
Why Developers Need Access to IBM MQ
Developers need access to IBM MQ to build, test, and troubleshoot effectively. In many organizations, teams restrict that access, which slows down development and increases dependence on operations teams.
Whether they are working on new features or debugging an integration issue, developers often need to interact directly with message queues. This includes the ability to:
- View the queues and messages they own
- Validate how messages flow between systems
- Troubleshoot integration issues in real time
Without direct access to IBM MQ, developers rely on admins or submit support tickets just to check queue contents or confirm whether a message was processed correctly. These delays create unnecessary bottlenecks and slow development cycles, especially in fast-paced environments where rapid iteration is essential.
At one major U.S. bank, development teams ran into exactly this problem.
This lack of visibility leads to real consequences:
- Delivery timelines slip
- Development teams grow frustrated
- Support requests pile up for middleware admins
For modern DevOps teams, this workflow is unsustainable. Developers need a way to work with IBM MQ that is fast, efficient, and secure. The challenge is enabling that access without compromising compliance or the integrity of the infrastructure.
The Challenge: Security and Compliance Limit Developer Access
Developers need access to IBM MQ, but administrators often say no, and they have good reasons for doing so. MQ environments support mission-critical systems. A single misstep can disrupt production, violate compliance policies, or compromise sensitive data.
Administrators typically control IBM MQ because of how deeply it integrates into enterprise infrastructure. Granting developers full access introduces real risks. These risks include:
- Misconfigurations that affect production queues
- Unauthorized message changes that break audit policies
- Violations of governance standards, especially in regulated industries
Most organizations want to support their developers. The problem is not a lack of willingness. It is a lack of the right tools. Traditional MQ tools follow an all-or-nothing model. They either grant full admin control or provide no visibility at all. These tools do not offer a way to give developers scoped, limited, or read-only access to just the parts of MQ they need.
As a result, teams fall into an inefficient cycle:
- Testing and validation efforts face constant delays
- Developers and MQ admins exchange frequent back-and-forth messages
- SLAs slip, and project timelines stretch
Modern teams need to move quickly, but they also need to stay secure and compliant. Developers must have access, and administrators must maintain control. Fortunately, there is a way to support both priorities without making sacrifices.
Infrared360: Putting MQ in Developers’ Hands (Safely)
Infrared360® solves the challenge of giving developers access to IBM MQ without compromising control, security, or compliance. It provides the visibility developers need and gives administrators the governance they require.
At the center of this solution is Trusted Spaces™, Infrared360’s role-based access control framework. It lets organizations define exactly what each user can see and do within the MQ environment. This ensures that developers only access the parts of MQ that are relevant to their work.
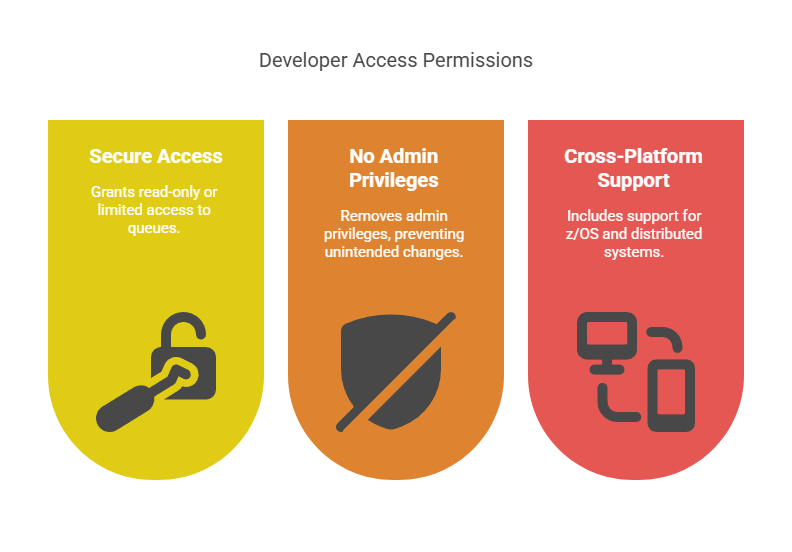
With Trusted Spaces, developers can be granted:
- Secure, read-only or limited access to specific queues and environments
- No admin privileges, removing the risk of unintended changes
- Cross-platform support, including both z/OS and distributed MQ systems
This balance between visibility and restriction empowers developers and protects critical infrastructure. Developers can interact with their queues, test message flows, and troubleshoot issues while staying within clearly defined boundaries set by administrators.
One large U.S. bank used Infrared360 to overcome this exact challenge.
The results spoke for themselves. Developers gained the insight they needed to move faster, and administrators maintained the security and compliance standards the organization required.
Let’s take a closer look at how Trusted Spaces works in practice and why it has become a game-changer for developer productivity.
Trusted Spaces™ Explained: Role-Based Access Without Risk
Trusted Spaces™ is what makes Infrared360® uniquely effective at bridging the gap between developer productivity and operational control. It allows organizations to grant precise, role-based access to IBM MQ. This access ensures developers can work efficiently while administrators protect the environment.
With Trusted Spaces, developers gain the tools they need to build and troubleshoot messaging integrations. This includes the ability to:
- Send test messages using synthetic transactions without deploying full applications
- Search queues and inspect message payloads to validate behavior and resolve issues
- View only the queues, topics, and environments assigned to them, with no additional exposure
This access remains tightly scoped. Developers cannot edit production objects or accidentally clear critical queues. Infrared360 customizes each developer’s view based on their role, team, or project. This design enforces the principle of least privilege and supports secure collaboration.
At the same time, administrators retain complete oversight. They:
- Control access rules and permissions
- Monitor complete audit logs and historical user activity
- Reduce support burdens by enabling developers to resolve issues independently
As one security lead at a U.S. bank explained:
Trusted Spaces is more than just a feature. It represents a strategic shift toward secure, scalable access. It enables developers to move faster while giving administrators the confidence to maintain full control.
Let’s look at some real-world results that teams have achieved by adopting this approach
Real-World Results: Faster Dev, Fewer Tickets
When developers gain the access they need without compromising security, both development and operations teams benefit. That’s exactly what happened when U.S. Bank adopted Infrared360® with Trusted Spaces™.
Yes, the U.S. bank we mentioned earlier really was U.S. Bank.
Before using Infrared360, developers at the bank had no visibility into MQ queues. Even basic testing or troubleshooting required opening support tickets, waiting for admin responses, and navigating frustrating bottlenecks. After the team implemented role-based access through Trusted Spaces, the workflow improved dramatically.
The bank saw several key results:
- Support ticket volume dropped significantly
- Developers validated message flows and resolved issues on their own
- Middleware administrators no longer acted as intermediaries and focused on higher-value work
This shift led to faster delivery timelines, smoother testing cycles, and stronger collaboration between development and infrastructure teams. Developers took more ownership of the build-and-test process, while administrators maintained full control over access, governance, and compliance.

This model creates an ideal balance.
✅ Developers innovate and move faster
✅ Admins stay in control
✅ Compliance standards remain intact
This outcome is not unique to U.S. Bank. Any team struggling with restrictive MQ access policies can unlock similar improvements. The key lies in providing the right kind of access, and that’s exactly what Infrared360 delivers.
Now, not every team starts with full-scale MQ environments or enterprise-grade tooling. Some developers are just getting started with IBM MQ and need a way to explore it safely. For those teams, IBM provides a free developer edition that helps them build familiarity with the platform before moving into more complex environments.
Getting Started with IBM MQ Developer Edition
The IBM MQ Advanced for Developers edition provides a great entry point for teams new to MQ. This free, non-production version includes all the core capabilities of IBM MQ. It works well for learning, prototyping, and experimenting in a local environment.
With this edition, developers can:
- Spin up a local queue manager
- Send and receive test messages
- Work with MQ’s APIs in languages such as Java, C#, and Python
- Learn how queue-based messaging works in a safe, isolated setting
You can download the IBM MQ Advanced for Developers edition here: IBM MQ Advanced for Developers Download
Although this version is ideal for sandbox testing, most development teams also need access to shared environments. These environments often include distributed and z/OS-based MQ instances, where stricter access controls apply. In those cases, traditional tools fall short and create barriers for developer productivity.
Infrared360 fills that gap. It extends controlled visibility and access to shared MQ environments, allowing developers to stay productive as their work scales. It does this without compromising security, governance, or operational integrity.
Back to That Queue You Couldn’t See…
You’ve seen it happen. A developer hits a wall because they can’t view a queue or validate a message. A support ticket goes in. An admin investigates. The clock ticks. Progress stalls.
It doesn’t have to be that way.
Teams no longer need to choose between empowering developers and protecting infrastructure. With the right tools in place, they can achieve both. Developers test, troubleshoot, and ship faster. Administrators maintain full oversight, enforce access boundaries, and meet compliance standards.
Trusted Spaces™ in Infrared360 makes this possible. It delivers scoped, role-based MQ access tailored to each user’s responsibilities—giving teams the control they need and the agility they want.
- Developers resolve issues without waiting
- Admins stay in control without becoming bottlenecks
- Organizations reduce friction while staying audit-ready
Your infrastructure already relies on IBM MQ. Now your developers can too.
Ready to empower your developers and protect your MQ environment? Call us at 973-826-7406.
More Infrared360® Resources