Best Practices for Securing IBM MQ in Kubernetes
As organizations modernize their infrastructure, deploying IBM MQ in Kubernetes has become increasingly common. But with this shift comes new challenges—especially in security. Traditional methods of access control and monitoring aren’t enough in dynamic, containerized environments.
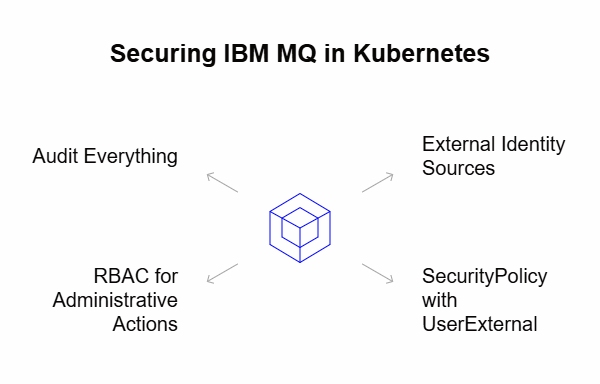
Securing IBM MQ in Kubernetes requires a focus on identity, visibility, and role-based access control (RBAC):
- Use external identity sources: In Kubernetes, container-based deployments don’t maintain persistent OS-level users. To maintain secure, centralized control over who can access queue managers, MQ should be integrated with external authentication systems like LDAP or OpenID Connect.
- Apply SecurityPolicy with UserExternal: This enables user mapping from external identity providers and removes the need to manage users inside each MQ container.
- Enable RBAC for administrative actions: Native MQ authorization via Object Authority Manager (OAM) is based on user-by-user definitions, which doesn’t scale in Kubernetes. Instead, use a solution that provides group-based permissions and scopes access based on roles.
- Audit everything: Containerized environments are highly dynamic. Real-time visibility into changes, access, and command activity is essential for compliance and security. A solution like Infrared360 can provide audit-ready tracking across all administrative actions, user logins, and configuration changes.
Get the Guide
By combining centralized identity, scoped permissions, and continuous monitoring, organizations can confidently secure IBM MQ in Kubernetes environments. But there is a lot more to securing modern MQ deployments in cloud, hybrid, containers, clusters, etc. Discover leading tips in our latest paper: Securing Modern IBM MQ® Environments
More Infrared360® Resources