ActiveMQ vs. RabbitMQ: Security Features and Best Practices
When selecting a messaging broker for enterprise environments, security is often one of the most critical considerations. When looking at ActiveMQ vs RabbitMQ security, there is a lot to consider. While many other options exist such as IBM MQ, and even some event driven solutions, ActiveMQ and RabbitMQ are still two widely used choices, each offering some features to secure message exchanges. In this blog, we’ll examine the key security features of both platforms and share best practices for implementing them in an enterprise context.
Overview of Security in Messaging Brokers
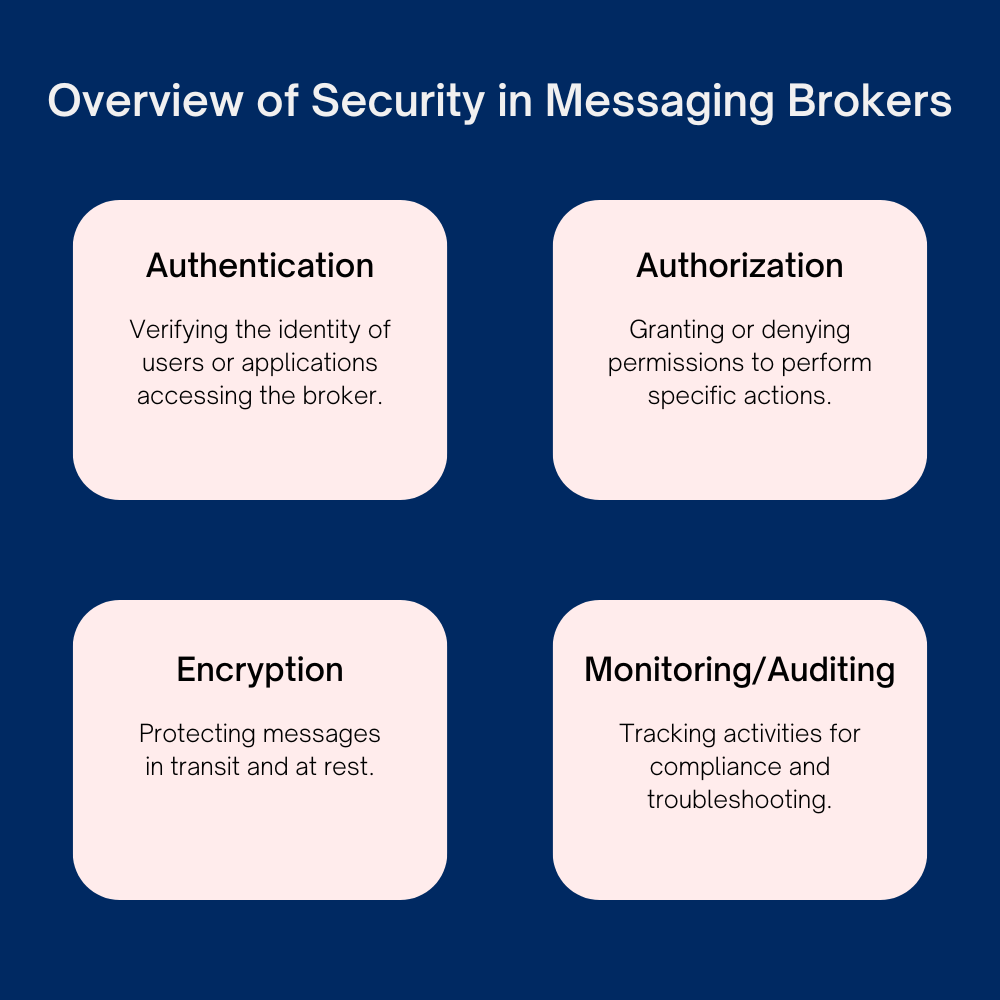
Messaging systems often handle sensitive data, making it essential to have strong security mechanisms. A comprehensive security strategy typically includes:
- Authentication – Verifying the identity of users or applications accessing the broker.
- Authorization – Granting or denying permissions to perform specific actions.
- Encryption – Protecting messages in transit and at rest.
- Monitoring and Auditing – Tracking activities for compliance and troubleshooting.
While other message-oriented middleware like IBM MQ may provide a more robust option for enterprises prioritizing security, both ActiveMQ and RabbitMQ remain strong contenders for organizations seeking lightweight, flexible messaging solutions that can adapt to their unique security needs. Read on for more details on how ActiveMQ vs RabbitMQ security features stack up.
Authentication Mechanisms
Authentication ensures secure communication by verifying users and applications accessing the broker.
- Built-In User Authentication: Both ActiveMQ and RabbitMQ support a simple user database for local authentication, suitable for smaller deployments.
- External Authentication: ActiveMQ integrates seamlessly with enterprise systems using JAAS, offering robust LDAP and Kerberos support for SSO. RabbitMQ also supports LDAP but expands its features with OAuth 2.0 and SASL mechanisms, which cater to modern, distributed architectures.
- Certificate-Based Authentication: Both platforms provide mutual TLS (mTLS) using certificates, ensuring secure identity verification.
- Custom Authentication: Both ActiveMQ and RabbitMQ allow custom authentication mechanisms through plugins, offering flexibility for proprietary systems.
Summary of Authentication Features
| Feature | ActiveMQ | RabbitMQ |
|---|---|---|
| Built-In User Database | Yes | Yes |
| LDAP Integration | Yes | Yes |
| Kerberos | Yes | No |
| OAuth 2.0 | No | Yes |
| SASL Mechanisms | Limited | Yes |
| Certificate-Based (mTLS) | Yes | Yes |
| Custom Authentication Plugins | Yes | Yes |
Both ActiveMQ and RabbitMQ offer a solid foundation for secure authentication, with overlapping capabilities in areas like LDAP integration and certificate-based authentication. However, again, ActiveMQ’s support for Kerberos might appeal to organizations deeply integrated with traditional enterprise authentication systems.
Note: When integrating middleware management solutions, it’s crucial to choose tools that work within your existing security framework, including authentication methods. This avoids introducing separate layers of security that could create unseen vulnerabilities. Leveraging your organization’s established security parameters ensures consistent protection and reduces the risk of gaps in oversight. This principle was central to our vision when we developed Infrared360 — a solution designed to seamlessly integrate with your existing security infrastructure for comprehensive and controlled middleware management.
Authorization Controls
Authorization defines what actions authenticated users can perform.
- Role-Based Access Control (RBAC): Both brokers offer RBAC; ActiveMQ focuses on resource-level roles, while RabbitMQ extends this with vHosts for logical isolation.
- Granular Permissions: ActiveMQ defines access rules for queues and topics, offering straightforward configuration. RabbitMQ adds regex patterns for dynamic control of permissions, beneficial for multi-tenant environments.
- Policy Management: ActiveMQ uses configuration file entries for precise control over behaviors like queue limits and access restrictions. RabbitMQ offers an accessible UI for applying and combining policies.
Summary of Authorization Features
| Feature | ActiveMQ | RabbitMQ |
|---|---|---|
| Role-Based Access Control | Yes | Yes |
| Granular Resource Permissions | Yes | Yes |
| Regex-Based Permissions | No | Yes |
| Virtual Host (vHost) Isolation | No | Yes |
| Policy-Based Control | Yes | Yes (more advanced) |
| External Authorization | Yes (via JAAS/plugins) | Yes (via LDAP/plugins) |
Both ActiveMQ and RabbitMQ offer robust authorization capabilities, but the specifics of their implementation vary:
- RabbitMQ stands out with vHost isolation and regex-based permissions, which provide powerful tools for managing multi-tenant environments and dynamically adjusting access rules.
- ActiveMQ, on the other hand, delivers a more traditional role-based system and relies heavily on external systems or plugins for advanced scenarios.
If your environment leans on traditional enterprise frameworks or simpler role-based models, ActiveMQ might align better with your requirements.
Encryption Support
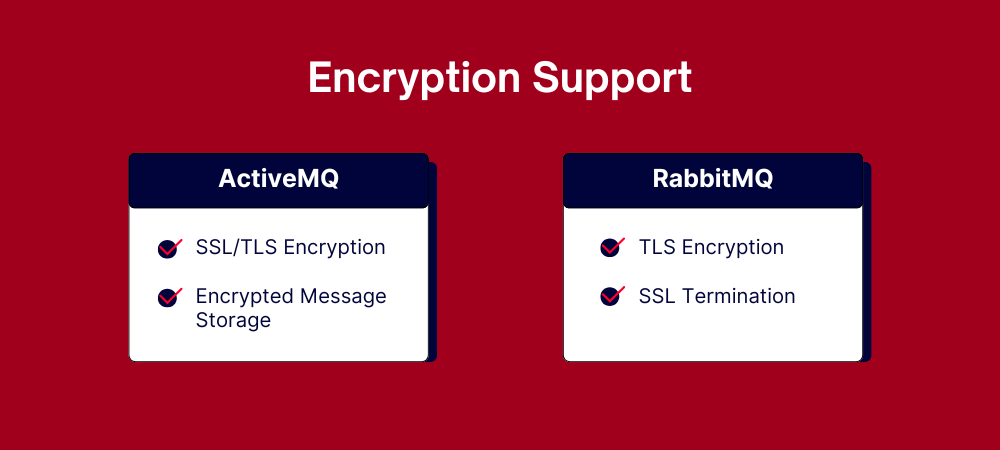
While both ActiveMQ and RabbitMQ offer robust encryption support through TLS for securing data in transit and optional tools for encrypting data at rest, ActiveMQ’s built-in flexibility with external plugins for message payload encryption gives it an edge for enterprises needing tailored solutions. RabbitMQ’s simpler SSL/TLS configuration is user-friendly but may require additional tools for more complex encryption needs, making ActiveMQ a better choice for advanced security requirements.
ActiveMQ
ActiveMQ ensures secure message transmission with:
- SSL/TLS Encryption: Protects messages in transit.
- Encrypted Message Storage: Allows optional encryption of message payloads at rest using external tools or plugins.
RabbitMQ
RabbitMQ uses:
- TLS Encryption: Secures connections between clients and the broker.
- SSL Termination: Ensures secure communication in hybrid environments with multiple broker nodes.
Monitoring and Auditing
Effective monitoring and auditing are foundational to securing enterprise messaging systems like ActiveMQ and RabbitMQ. Both platforms offer basic tools to track system activity, but their native capabilities fall short when it comes to providing the deep, real-time visibility required for robust security. Monitoring for potential threats—such as unauthorized access or unusual message traffic—combined with auditing user activities, is critical to identifying vulnerabilities and ensuring compliance. For enterprises comparing ActiveMQ vs. RabbitMQ security, understanding these tools’ limitations underscores the need for third-party solutions that integrate advanced monitoring, comprehensive auditing, and proactive threat detection into a unified interface.
1. ActiveMQ vs RabbitMQ Security Monitoring Capabilities
- ActiveMQ: ActiveMQ relies on JMX (Java Management Extensions) for monitoring, offering insights into broker performance, queue depth, message throughput, and resource utilization. However, JMX requires external tools for visualization, such as JConsole or Prometheus, and lacks a unified dashboard for administrators.
- RabbitMQ: RabbitMQ includes a Management UI and RESTful API for monitoring key metrics like queue sizes, message rates, and connection states. While its interface is user-friendly, it primarily focuses on operational metrics and does not provide in-depth insights or predictive analytics.
Comparison: While both platforms provide basic monitoring, neither offers comprehensive visibility across hybrid or containerized environments. They also fail to integrate advanced monitoring features like real-time anomaly detection and granular alerting parameters within their native tools.
A robust solution should unify monitoring across middleware systems, provide synthetic transactions to simulate real-world message flows (including scheduling capabilities) for testing, and offer advanced dashboards for deeper insights—all in a single interface. In today’s security conscious business environment, a standalone monitoring tool is no longer enough. The ability to consolidate monitoring, responses to alerts, and even automation of those responses within a single interface has become a necessity for cost-effective, efficient, and secure operations.
2. Auditing and Security Monitoring
- ActiveMQ: ActiveMQ supports auditing through custom plugins or by logging user activity, such as login attempts and message accesses. While this approach provides some flexibility, it is fragmented and requires significant manual configuration, ultimately making it insufficient for meeting stringent compliance standards in its native form.
- RabbitMQ: RabbitMQ offers basic audit logs that capture user actions like queue creation or message publishing. However, these logs lack advanced filtering and correlation capabilities, further limiting their usefulness for enterprises with robust compliance and security requirements.
Comparison: Both brokers fall short in providing comprehensive native auditing capabilities. ActiveMQ’s customizable plugins allow for greater adaptability to specific needs, but its reliance on manual setup highlights the inherent limitations of its native tools. RabbitMQ’s straightforward logging, while functional, offers even fewer options for meaningful analysis and reporting.
For effective security and compliance, enterprises require detailed tracking of user activities, role-specific access reports, and actionable insights—all integrated into a single platform. Neither ActiveMQ nor RabbitMQ delivers these capabilities natively. A third-party solution is recommended to provide unified monitoring, auditing, and administrative tools, ensuring efficiency, visibility, and compliance across complex environments.
Security Related Administrative Tools
Administrative tools are vital for managing the complex configurations and operations of any messaging broker, including ActiveMQ and RabbitMQ. These tools streamline essential tasks such as queue management, topic configurations, and permission settings. However, native tools often lack integration and may require multiple interfaces or external scripts to achieve comprehensive management. This fragmented approach can lead to inefficiencies and errors, particularly in large-scale or multi-tenant environments. A robust administrative solution should combine monitoring and management capabilities in a unified interface, simplifying workflows and enhancing operational control.
- ActiveMQ: Administrative tasks in ActiveMQ, such as managing queues, topics, or configurations, are often performed via scripts or external tools, creating a disjointed workflow.
- RabbitMQ: RabbitMQ’s Management UI allows basic administrative tasks like creating queues or managing permissions. However, its RBAC implementation lacks the granularity required for complex environments.
Comparison: Neither platform provides a seamless integration of monitoring and administration capabilities in a single interface, forcing administrators to switch between tools and increasing the potential for errors.
Here, too, a more comprehensive 3rd-party solution is recommended. An integrated solution simplifies workflows by combining monitoring and administration in one interface. Granular RBAC ensures users only access what they need, enabling secure multi-tenant management and reducing operational overhead.
Role-Based Access Control (RBAC)
- ActiveMQ: ActiveMQ relies on external plugins or custom configurations to implement RBAC, often requiring significant manual setup to achieve multi-user isolation.
- RabbitMQ: RabbitMQ offers RBAC via virtual hosts (vHosts) and permissions, but this approach becomes complex and cumbersome in large deployments.
Role-Based Access Control (RBAC) is essential for ActiveMQ, RabbitMQ, and any message-oriented middleware to ensure secure and efficient operation in multi-user environments. For both ActiveMQ and RabbitMQ there are robust 3rd-party solutions available for RBAC. Caution, however that an effective solution must provide granular RBAC that enables fine-tuned combinations of visibility controls and access controls. Capabilities like self-service administration for end users further enhances efficiency and security and for a solution to provide that it must be capable of a wide range of administrative functions and advanced monitoring capabilities under the same interface.
Performance Testing
While neither ActiveMQ nor RabbitMQ offers fully integrated, user-friendly native tools for comprehensive performance testing as part of their standard feature sets, each provides basic utilities to simulate workloads. These tools often require manual setup and expertise to deploy effectively.
- ActiveMQ: ActiveMQ includes performance testing capabilities through its built-in JMS performance modules. These tools allow users to simulate message flows and measure broker performance under varying conditions. However, these features are not designed for ongoing, automated performance validation and often need additional configuration and external tools for advanced scenarios.
- RabbitMQ: RabbitMQ provides PerfTest, a command-line utility that generates synthetic workloads by simulating producers and consumers. While useful for benchmarking throughput and latency, PerfTest lacks integration with other monitoring or administration features, limiting its usability in production environments.
As it is with any message-oriented middleware, performance testing is critical for ensuring reliability and scalability. Neither ActiveMQ nor RabbitMQ delivers a seamless, integrated approach to performance validation. A third-party solution is recomended to continuously test and optimize message flows, simulate production-like conditions, and provide actionable insights. This unified approach ensures a proactive stance in maintaining system performance and reliability.
The Case for Third-Party Tools
While ActiveMQ and RabbitMQ provide adequate tools for basic monitoring, auditing, and administration, their native capabilities fall short for enterprises requiring deep insights, comprehensive auditing, or integrated management workflows. Here’s why a third-party solution like Infrared360 is essential:
- Unified Interface: Combines monitoring, auditing, and administration in one platform, eliminating the need to switch between tools.
- Granular RBAC: Ensures secure, role-specific access, allowing organizations to enforce strict compliance and multi-tenant isolation.
- Advanced Auditing: Tracks every user action, from administrative changes to message handling, with detailed reports for compliance.
- Synthetic Testing: Proactively identifies potential issues by simulating message flows and high-traffic scenarios.
- Scalability: Extends visibility and control across hybrid, containerized, or multi-broker environments.
For organizations seeking a complete solution to manage their messaging infrastructure effectively, a purpose-built third-party platform is not just a convenience, it’s a necessity.
Best Practices for Securing Messaging Brokers
- Use Strong Authentication: Always prefer external authentication systems like LDAP or OAuth for scalability and centralized management.
- Enforce RBAC: Assign roles and permissions to users to minimize access to critical queues or topics.
- Enable Encryption by Default: Configure SSL/TLS for all broker connections to secure data in transit.
- Monitor Activity: Use the provided monitoring tools to track suspicious activities and maintain compliance with regulations.
- Keep the Broker Updated: Apply security patches regularly to safeguard against vulnerabilities.
Conclusion
Both ActiveMQ and RabbitMQ offer varying security features, making them reliable choices for enterprise messaging. The best choice often depends on your existing infrastructure and specific security requirements. By following best practices like enforcing RBAC, enabling encryption, and leveraging 3rd-party monitoring and administration tools, organizations can ensure secure and efficient messaging in their environments. For more information on a robust, comprehensive monitoring and administrative solution for ActiveMQ and other Middleware, visit Avada Software’s ActiveMQ administration page.
More Infrared360® Resources