The Importance of Access Controls in MQ Incident Response
IBM® MQ plays a critical role in ensuring reliable, secure messaging between distributed applications. But as your MQ infrastructure grows in complexity—spanning hybrid, containerized, and multi-cloud environments—so too does the risk of misconfiguration, unauthorized access, and slower incident response times. That’s where access controls in MQ become more than just a checkbox on your security audit—they’re a frontline defense and a critical enabler of effective incident response.
The Role of RBAC in Collaborative Issue Resolution for MQ
Role-Based Access Controls in MQ (RBAC) plays a crucial part in accelerating incident resolution while maintaining strict governance over sensitive messaging infrastructure. RBAC ensures that each user—whether part of the application, middleware, operations, or security team—has access only to the MQ objects, queues, and administrative actions necessary for their role.
This not only enhances security by limiting exposure but also fosters faster, safer collaboration during time-critical events like queue build-ups, channel failures, or message delivery delays.
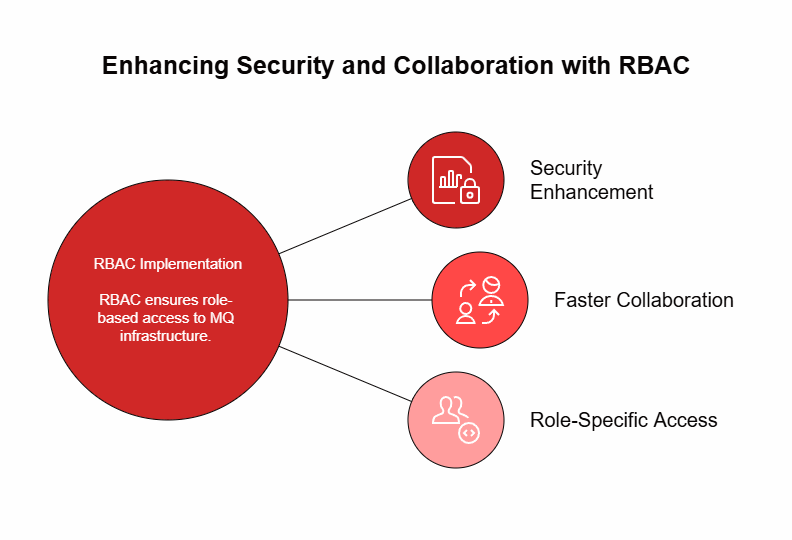
A Help Net Security report underscores the value of scalable permission models in incident response. It highlights features such as group-based permissions, private incident handling, and Single Sign-On (SSO) integration—all of which are particularly important in environments where multiple teams may need to interact with MQ systems during a crisis. RBAC ensures that only the right people have visibility and control, reducing errors and helping organizations meet compliance requirements.
Similarly, Splunk emphasizes that RBAC simplifies access management and supports streamlined collaboration. In the context of IBM MQ, this translates into defining precise roles for queue browsing, message movement, or configuration access—empowering each team to contribute to resolution efforts without waiting for admin-level intervention or risking over-permissioning.
When implemented properly—especially with a centralized MQ monitoring and administration tool like Infrared360®—RBAC not only safeguards your infrastructure but becomes a strategic enabler for agile, secure incident response.
Real-World Example: Access Controls Enable Faster Recovery
Take the example of Alight, a large-scale IT services provider. They were facing serious challenges with MQ administration, including fragmented tooling, security compliance issues, and high maintenance overhead. After replacing their legacy setup with Infrared360, they reported the following improvements:
- Simplified secure access across teams: With Infrared360’s group- and role-based permissions, Alight enabled technical users to view and manage their own queues securely—without needing customized mini-apps or manual admin work.
- Reduced operational complexity and overhead: Infrared360’s agentless design allowed centralized monitoring across all platforms without installing agents or adapters, dramatically lowering maintenance burden
- Enhanced visibility and incident response: Teams gained the ability to quickly browse queue contents and debug issues in real-time. This replaced limited homegrown scripts and significantly improved issue triage and response time.
This real-world implementation illustrates how access controls in MQ not only protect systems but enable faster, coordinated incident response—without compromising compliance or introducing risk. Check out the full case study here.
The Cost of Delay in MQ Incident Response
Middleware like IBM MQ is the connective tissue between systems. As a result, it’s often at the root of investigation when performance or security issues crop up. When an incident occurs in MQ, whether it’s message build-up, unexpected downtime, or suspicious access behavior, cross-functional collaboration is essential to determine whether the problem is in the middleware or if it’s an application or network issue.
For example: imagine an enterprise financial services firm relying on IBM MQ to process thousands of time-sensitive transactions per minute. Suddenly, the system slows down—confirmation messages lag, transaction times spike, and service-level agreements (SLAs) are at risk. An urgent incident is declared. Resolving it quickly demands tight collaboration across multiple teams, each with a different lens—but all needing access to specific parts of the MQ infrastructure.
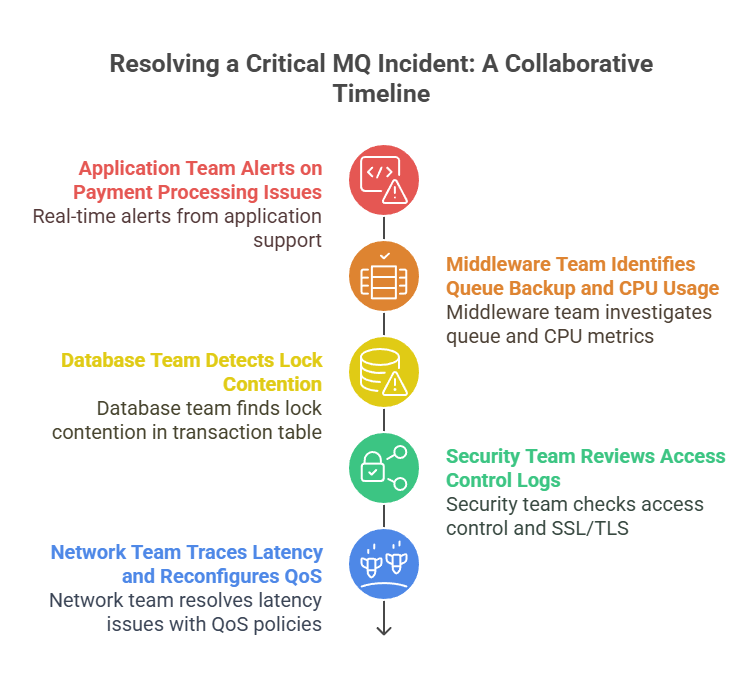
Application Team: The Frontline Observers
The first alerts come from the application support team. Their payment processing service is timing out while waiting for confirmation messages. After checking logs, they discover that their app is failing to PUT messages onto a reply-to queue managed by IBM MQ. At first glance, it appears to be a bug in their retry logic. But they also suspect increased queue depths or blocked channels might be contributing. They escalate to the middleware team and request real-time visibility into the queue to confirm their theory—visibility they don’t currently have.
Middleware Team: Message Flow Investigators
The MQ team eventually notices that the confirmation queue is backed up, and the queue manager is reporting inhibited PUTs due to max queue depth. They check channel status and find one of the consuming services isn’t active on its channel, suggesting a downstream bottleneck. Additionally, one of the queue managers in the cluster shows high CPU usage, pointing to a potential load balancing issue or message affinity misconfiguration.
Database Team: Root-Cause Context
The downstream consuming application depends on a relational database to store transaction confirmations. The database team inspects performance metrics and identifies lock contention on a key transaction table, introduced by a recent indexing change. Because the consuming service can’t write fast enough, it’s unable to acknowledge messages in MQ. This causes messages to pile up, triggering PUT failures upstream and halting new transactions—a cascading failure rooted in delayed message consumption.
Security Team: The Watchdogs
To rule out tampering or cyber threats, the security team reviews MQ access control logs and SSL/TLS configurations. No evidence of compromise is found, but they do detect a misconfigured CHLAUTH rule on one of the channels that could prevent reconnects if the load increases further. They adjust the rule and review RBAC permissions in place—verifying that only authorized service accounts have access to the affected queue managers and queues.
Network Team: Latency Sleuths
Finally, the network team is brought in to trace latency in channel connections. They identify a congested network switch between the queue manager and the consuming service, causing intermittent channel drops. After reconfiguring QoS policies to prioritize MQ traffic, message flow begins to normalize.
Why Collaboration Depends on Access Controls in MQ
Access bottlenecks slow down resolution. Admins often become gatekeepers, scrambling to grant temporary permissions or run commands on others’ behalf. This results in delays, miscommunication, and a fractured response process.
Role-Based Access Control (RBAC) changes the game. When you implement granular RBAC across your MQ estate:
- Each user or team has the exact level of access they need—no more, no less.
- Access to queue managers, channels, and queues can be scoped to environment (e.g., Dev vs. Prod), geography, or business unit.
- Incident responders can self-service their investigation without compromising sensitive systems or data.
In short: RBAC enables secure collaboration. It streamlines handoffs, reduces risk, and supports faster mean-time-to-resolution (MTTR).
The Triad of MQ Security: SSL, CHLAUTH, and RBAC
As detailed in our whitepaper Securing Modern IBM MQ Environments, incident response doesn’t start when something breaks—it starts with how you structure your MQ environment in the first place.
In secure and modern MQ deployments, three pillars form the foundation of proactive, collaborative incident response:
Want the technical breakdown?
Incident Response Is a Team Sport—Infrared360 Makes You a Better Coach
The faster you can identify, isolate, and remediate an MQ issue, the less impact it has on your business. Infrared360 not only helps monitor MQ in True Real-Time™, but empowers teams to act, securely and independently, based on their role and scope.
Here’s what Infrared360 brings to your incident response toolkit:
- Scoped RBAC with Trusted Spaces™ for granular access control
- Audit trails to track who did what and when
- Real-time alerts on cert expirations, channel states, queue depths, unauthorized access attempts, and more
- Self-service administration (with guardrails!) so DevOps, App Teams, and SREs don’t wait for MQ admins
And thanks to native integrations with ServiceNow, Grafana, and others, it fits directly into your enterprise response workflows.
Don’t Wait for the Next Incident
Your MQ environment is only as secure—and as resilient—as your access strategy. With Infrared360, you don’t just detect problems faster; you resolve them faster, with the right people having the right access at the right time.
Ready to take the next step?
- Download the full whitepaper: Securing Modern IBM MQ Environments
- Book a live demo of Infrared360® and see how it can elevate your MQ security and incident response.
Access controls in MQ aren’t just about compliance—they’re your secret weapon for speed, security, and success when incidents strike. Let Infrared360 help you put them to work.
More Infrared360® Resources